According to Statista, 48% of software developers around the globe rate the importance of DevOps to scaling software development as “extremely important.” This shouldn’t come as a huge surprise as 63% of developers and DevOps experts state the quality of their software deployment has improved significantly along with the frequency of new software releases, while 55% report improved cooperation and collaboration, with 38% saying the quality of code production has increased since they’ve started deploying DevOps.
However, the DevOps Institute Upskilling report for 2020 reveals that the adoption of the DevOps approach is deemed “very difficult” for more than 50% of companies surveyed, with many of them stating security-based issues as one of the main pitfalls of this strategy.
When we factor in a recorded 87% increase in malware infections over the last 10 years, the number of recorded malware attacks reaching 20.4 billion in 2018/2019 alone, as well as the number of cyberattacks attacking companies increasing by 200% in 2019, we can clearly see why the evolution of DevOps is gravitating toward security.
Hence the advent of DevSecOps.
The Need for the Security-First Mindset
Gone are the days when the devs’ only purpose was sheer coding. In order to achieve a highly functional framework, the developer needs to pay close attention to the security layer as well, aside from working towards creating highly functional and stable code. The DevSecOps (also referred to as SecDevOps, the disambiguation of the two is addressed later in this article) places the developer in the fulcrum position within an application security strategy.
In order to resolve the vulnerabilities of the DevOps-based software development and bridge the gaps in feedback loops caused by the need for shorter development cycles, security risks should be addressed and tackled more homogeneously within the process of software development. In other words, the security shouldn’t be handled at the final stages of the development lifecycle, but throughout the entire process.
This need for the omnipresence of security created the landscape for the DevSecOps (or SecDevOps) approach wherein the overarching objective is to make security within SDLC as important as the speed and quality of the coding process.
How Does DevSecOps Work?
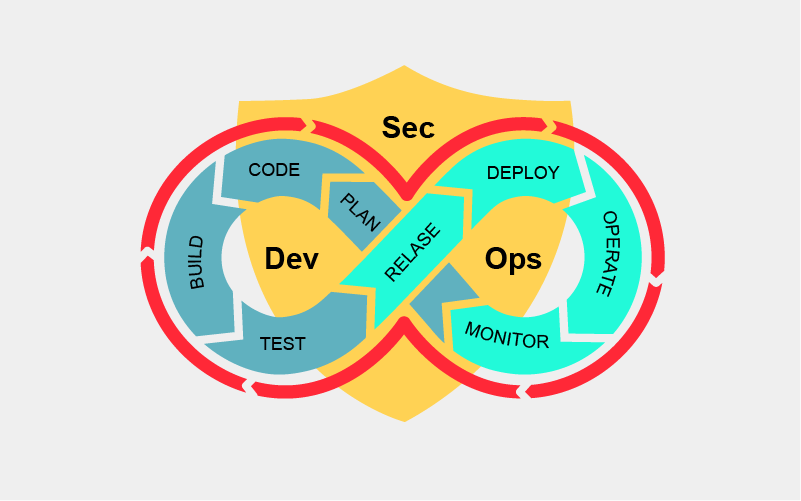
The DevSecOps mindset encompasses an inevitable shift towards imbuing security into the rapid-release software development ecosystem, therefore incorporating the shift-left mentality across organizations rather than resorting to having automated security processes or a dedicated team resolving these issues.
The following are some of the critical SecDevOps steps a company should take in order to make security a priority in a consistent manner:
- Thorough documentation and implementation of security requirements
- Consistency of building security into design activities
- Taking security into account prior to any code writing
- Placing security as the first and foremost objective within the test development and execution environment
- Addressing security whenever there’s a change introduced into a system
This allows for security to become a responsibility that will permeate all team members and development stages instead of being tackled by a separate team at the end of the cycle. DevSecOps makes sure security is among the main tasks the development team is responsible for, therefore addressing all security issues on-the-fly and mitigating the vast majority of potential problems later in the development life cycle.
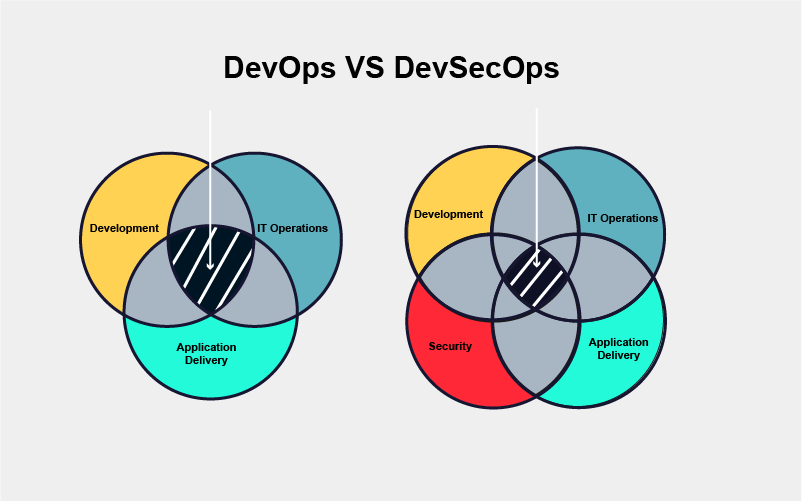
SecDevOps Vs DevSecOps: The Disambiguation
Some may argue there is a significant difference between DevSecOps and SecDevOps, mainly regarding the latter supposedly “putting security first” within the SDLC and going even further to focus on secure coding practices. However, the majority of the community agrees that DevSecOps and SecDevOps (sometimes even DevOpsSec) are interchangeable terms as the main idea behind both notions is to embed security into every single stage of the software development life cycle and account for the same set of advantages.
Which brings us to…
The Benefits of DevSecOps Implementation
By making security a vital component in each and every phase of the development process, the developers are able to provide the following benefits:
→ Faster Delivery
By making security an integral part of the SDLC, the team is capable of removing the entire security testing phase, thus increasing the delivery speed. Although this methodology may slightly slow down all other SDLC stages, the DevSecOps delivery time is still shorter when compared to regular DevOps, provided the DevSecOps strategy has been deployed in an optimal manner for your specific project/infrastructure.
→ Improved Overall App Security
The fact that your entire app development process incorporates rigorous and more continuous security testing on a more granular level, your end product ends up having a more stable and secure architecture overall. The teams that have the ability to identify and correct code vulnerabilities earlier in the process, slowly but surely become more capable of mitigating recurring mistakes during subsequent projects. As the app is being developed with security in mind at all stages of the SDLC rather than at the final stage, the overall security stops being a variable and becomes a constant.
→ Balanced Responsibility & Improved Teamwork
Traditional software development processes don’t typically have even levels of responsibility across all teams and team members, especially when it comes to security-based issues. Instead, the organization’s dedicated security team carries all the burden of potential problems emerging in the post-development stages. The SecDevOps approach shifts the security responsibility to the left and therefore balances it out. This allows for improved communication between the teams and team members, which further enhances the quality of security design patterns and makes security response strategies more reactive.
→ True Automation of Security
Reaching true automation levels in terms of security can be difficult within the regular DevOps environment. The SecDevOps approach, on the other hand, allows for an environment where you can reach, incorporate and successfully practice top-tier automation as the security- and testing-based tasks are incorporated from the very beginning of your SDLC. It also helps with the reduction of security gaps present within your IaC technologies.
How to Implement DevSecOps in 5 Basic Stages
1) Define Your End-Goal(s)
Prior to making any actual steps toward the implementation of the SecDevOps pipeline, it is critical to have a clear overview of what your main end-goals are. What you want to achieve and what the final result of your project is should be clear to all team members right from the start. Otherwise, it is highly likely you won’t be able to devise an effective and optimized DevSecOps strategy and your workflow may struggle.
In order to avoid this scenario, your team should pay close attention to both the technical details of your methodology, as well as the overall mindset of your teams – all the while focusing on the desired outcome. Be sure to take the following SecDevOps components into account right from the start:
- Resource sufficiency
- Shared accountability & responsibility
- Key milestones
- Constant communication
- Iteration-driven progress
Rarely are custom-tailored DevSecOps strategies perfect right from the get-go. They require maturing over time. But the clearer your end-goals are, the less obscure your strategy gaps will be.
2) Educate Teams & Assume the Leading Roles as Developers
Make sure your teams and team members are familiar with all security practices within the DevSecOps ecosystem and educate each employee about what their personal role in the workflow is. Each developer should have a straightforward role in this granular approach to boosting security, especially when compartmentalized teams are working on smaller code segments that should later be assembled to create a larger structure.
This is why the devs should be given a chance to take the lead and deploy a more holistic approach to the future-proofing of code security. They will know what needs to be done in order to embed proper security layers in each snippet of the greater project.
3) Assess Your Current Security Portfolio (Inventory, Pipeline, Tools, etc)
Jumping directly to a DevSecOps-based model is not possible without previously establishing major workflow gaps that need to be bridged. This requires a detailed understanding of what is currently in your company’s security portfolio and whether total rollback is necessary. This assessment should involve the creation of your teams’ inventory of all existing components, including:
- The list of DevOps and security tools (third-party, open-source, proprietary, etc)
- The original purpose of each tool
- The risk each tool should be mitigating/decreasing
- How capable each tool is of integrating with cloud provider APIs, along with the openness of its own API and the capability of generating/sharing contextual threat intelligence
- Cost-effectiveness in terms of how much you are paying for the particular tool, as well as your teams’ ability/skills to leverage the power of the tool
4) Bridging the Framework Gaps
Whether your company deploys control frameworks (like Center for Internet Security’s CIS-20 or NIST Cybersecurity Framework for example) or has a risk-based framework, it is probably a good idea to overlay this data using the tools from your inventory and your code movement patterns (the patterns by which your code and changes are going into the cloud).
Be sure to use industry standards for your gap analysis process. This should help you better understand framework/tools/control overlaps and gaps, as well as assist you in your shift from moving from an incoherent ecosystem of security solutions to an organized environment of comprehensive platforms that suit your unique framework.
5) Iterate Quickly & Constantly
The DevSecOps methodology yields the best results through constant iteration. Be sure to apply all the knowledge and experience you gleaned during the process of gap analysis and apply that data to your code pipeline. It is highly recommended that your team uses appropriate platform-based cloud security controls for your SecDevOps strategy and quickly learns what needs to be removed from the framework and workflow. If it involves removing certain point products that slow down and overburden your productivity, so be it. The main goal is to establish solid communication channels between the devs and the IT operations so the necessary security-based processes and platforms are incorporated into the least-disruptive components of your code pipeline.
Let's Bring Sec To Your DevOps
Our security experts will properly infuse security policies, tooling, and practices into your DevOps.
Learn morePotential Challenges With the DevSecOps Enablement
Utilizing too Many Tools
If your teams are not sufficiently familiar with the SecDevOps approach, it is probably a good idea not to enable too many tools within your SDLC. Instead, it is recommended that you only use the necessary tools at first so your team members can get familiar with the process more easily, and then add more tools as your team’s ability to leverage the most out of these platforms progresses.
Slow Methodology Adoption
Certain organizations may find the SecDevOps adoption process to be too slow, especially if they do not incorporate professional outside assistance. Although fully adopting this mindset and culture takes time, especially for teams that have trouble staying consistent with all the industry-specific DevSecOps methodology norms and compliances, keeping your team members up-to-date with future-proof technologies and patiently tutoring them is the way to go.
Wrapping Up
Bear in mind that a fully-optimized DevSecOps workflow isn’t easy to reach. There’s some low-hanging fruit to be harvested. After that, it takes time for your SDLC to reach maturity, obviate bottlenecks, and successfully embed security in each stage.
More integration leads to more dependencies, and there will always be both challenges and opportunities. As long as you focus on top-tier communication and streamlined collaboration between the teams – the speed, cost-efficiency, and innovation won’t be far behind.
