Table of Contents
When you plan to migrate to a new IT environment, such as the cloud, you have to ask yourself: can I protect my data and my infrastructure from misuse and how to do it? After all, you don’t know exactly where your data is stored at any given time and on which hardware your machines are running. And if you don’t know that, how can you know it is safe? What if you’re required to be compliant with some strict rules for securing your data, like HIPPA and PCI DSS??
So, what should you be aware of, when it comes to cloud security?
Keep reading.
Shared Responsibility Cloud Security Model
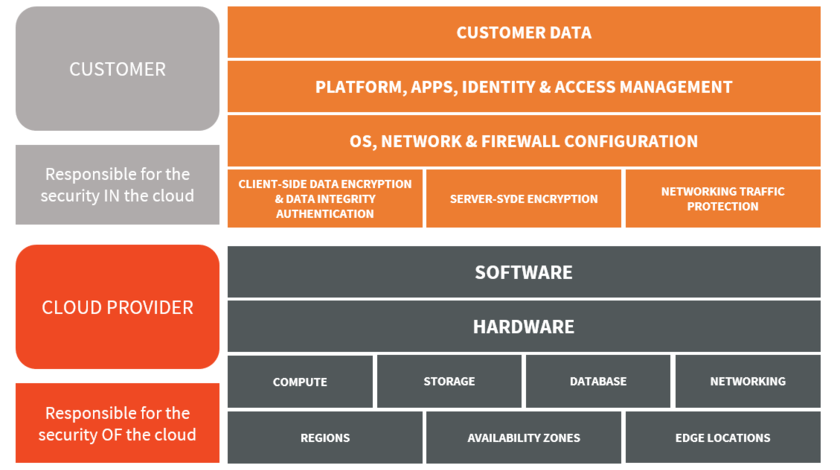
Every major cloud provider (Amazon Web Services, Microsoft Azure, Google Cloud Platform) offers what is known as Shared responsibility security model. This means that they, the provider, are responsible for securing all those services and infrastructure they fully control and provide to you, the customer. You are responsible for the stuff you provide – the configuration of virtual machines and apps, your code and your data.
However, cloud providers do provide you help in doing your part in the form of guidelines for secure design best practices, configuration options to tighten the security of your data, and tools to monitor, test and manage your overall cloud security.
The shared responsibility security model unburdens you with the daunting task of securing the entire system. It also introduces you with the additional need to trust your cloud provider to properly fulfill their responsibilities. But you should bear in mind one important thing: most cloud providers, and certainly the Big Three (AWS, Azure, GCP) do use the same cloud infrastructure for their own businesses. Their size and importance in the tech business also ensure that they can and do attract the best experts in various areas, including IT security, as well as to deploy the best and often the most expensive hardware and software tools to protect their infrastructure. They also constantly improve their systems and ensure, through internal and external auditing, that they are officially compliant with security standards such as HIPPA and PCI DSS.
Secure design best practices
As we all know, securing your data and your system starts at the designing phase. Whether you’re creating a totally new architecture for your exciting new app that you plan to run on the cloud, or you’re migrating parts of or your entire IT system to the cloud, you should plan for the security of your system. Since you’ll be using already present infrastructure (network, hypervisors) and specific services (databases, storage, messaging services), you have to be familiar with how they operate and how you should use them in the most secure way. These descriptions and guidelines are freely available on their websites for you to study and implement, and therefore make sure your cloud security is at maximum level.
Infrastructure security
Cloud infrastructure services provide ways to implement known security design principles when creating their own environments. Network isolation, access control, firewalls, separating users, defining security and service roles and encryption in transit and at rest, all provide the possibility of employing the principle of least privilege. This way you can control who can access your apps and data and what they can do with them. Naturally, the cloud provider cannot prevent you to mess up with your setup, but if you follow the best practices you should end up with a rather secure environment.
Cryptographic services and key management
Most cloud providers provide various cryptographic services that allow you to easily set up encrypted transit and encryption of data at rest. These services include even FIPS-certified HSMs (Hardware Security Modules). Also, you can now decouple access credentials for your back-office services (ie. databases) from your application code and thus ensure that an attacker cannot harvest these credentials from your code repositories. Key management for encryption and signing services is also implemented and you can set up retention policies for your keys.
Improving cloud security through monitoring and auditing
Security is a process and it lasts for the entire lifecycle of your environment. Therefore, it is paramount to monitor and log all access, events, and changes that happen in your environment. You should also implement auditing of your users and at all times have the opportunity to know exactly what is happening in your system. Most cloud providers implement extensive auditing, monitoring, and logging services that can help you collect, manage, search and analyze your logs. You can set up alerts to react to specific security events, search for anomalies and even use ML (machine learning) services to help you improve the security and protection of your data.
Security services that help you do your part
According to the shared responsibility security model, you are responsible for your part in the system: your apps, configurations, and data. Cloud providers will, however, provide services that will help you test and analyze your settings. Some services even utilize AI and ML to detect anomalies and possible intrusions, including compromised hosts and hosts that mine cryptocurrency. You can schedule vulnerability assessments that will automatically generate reports.
Managing cloud security
The Big Three provide security command and control centres that will help you manage your various security services from one point. Therefore, you don’t need to set up a separate system for your IT security teams. They will have an easier job of continuously monitoring your services and responding to incidents. This way you can have a ready-to-use SIEM service, or enable your existing SIEM software to access and analyze your logs and audit trails.
